Privacy by Design: Zero-Knowledge Pseudonyms for Supplier Collaboration
- gsriram87
- Sep 24, 2025
- 3 min read
Supply chain collaboration has always wrestled with a central tension: OEMs need transparency, while suppliers fear exposing sensitive details such as costs, production processes, or financial health. This fear often prevents suppliers from sharing the very information that could strengthen the ecosystem. The question is, how do we enable collaboration without compromising privacy? The answer lies in designing systems where privacy is embedded from the start—Privacy by Design.
The Privacy Trust Challenge
Traditional approaches to supply chain trust relied on nondisclosure agreements, audits, and central databases. While useful, these mechanisms fell short in global, multi-tier ecosystems. Audits were costly, NDAs unenforceable across borders, and central databases created disputes about who owned the ‘truth.’ Blockchain solved part of this by offering immutable, tamper-proof records, but it introduced another question: how do we preserve supplier privacy while ensuring trust?
Zero-Knowledge Pseudonyms Explained
Zero-Knowledge (ZK) proofs allow a party (the supplier) to prove that a statement is true without revealing the underlying data. When combined with pseudonymization, suppliers can share proof of compliance—emissions below a threshold, certified material composition, or financial solvency—without exposing sensitive details. This approach solves the trust gap while respecting confidentiality.
Think of it like showing your ID at a bar to prove you’re over 18, without sharing your exact birthdate, home address, or ID number. The verifier gets assurance, the supplier keeps privacy.
How It Works in Supply Chains
The flow of Zero-Knowledge pseudonyms in supply chain collaboration can be illustrated as follows:
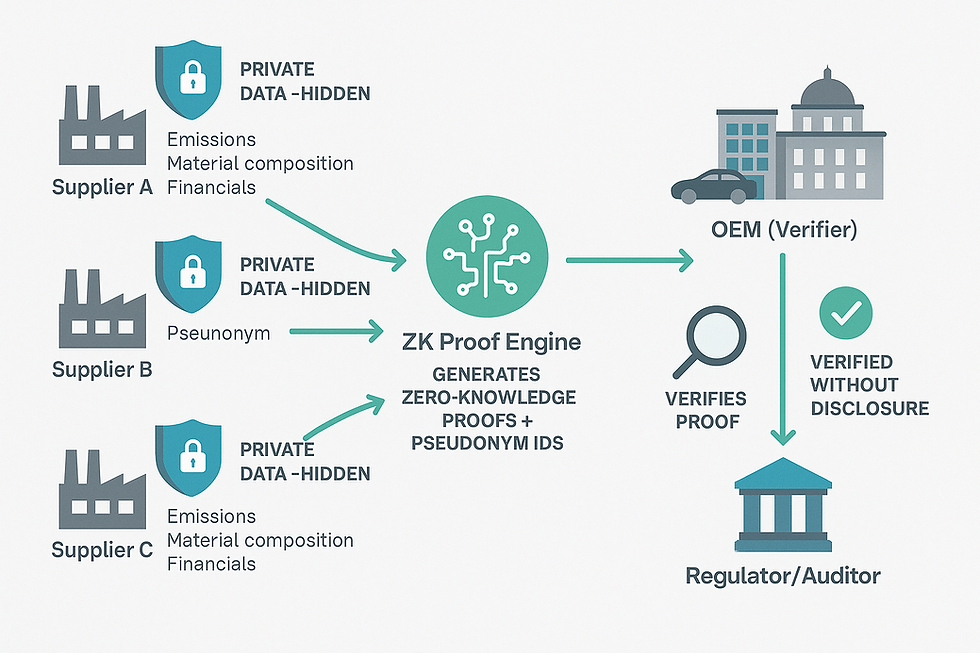
Figure: Event flow showing suppliers generating ZK proofs that OEMs and regulators can verify without accessing raw data.
Why ZK Proofs Are a Strong Starting Point
ZK proofs are not the only privacy-preserving technology—homomorphic encryption and multiparty computation (MPC) also exist. But ZK is a mature, practical entry point for OEMs. It has established frameworks, real-world adoption, and is easy to explain to suppliers: you prove compliance, but don’t reveal everything. That simplicity makes it an effective first step for OEMs wanting to bridge the trust gap with their strategic suppliers.
Technical Deep Dive (Without Heavy Cryptography)
At a high level, ZK proofs involve three components:- The Prover: the supplier generating the proof.- The Verifier: the OEM or auditor validating the proof.- The Proof: a cryptographic artifact that demonstrates compliance.Types include zk-SNARKs (succinct, fast verification) and zk-STARKs (transparent, scalable). Each has trade-offs in terms of performance, proof size, and trust assumptions. For supply chains, scalability and ease of integration are critical—proofs must be lightweight enough to work across thousands of suppliers.
For those interested in a deeper dive, see Vitalik Buterin’s [zk-SNARK introduction](https://vitalik.eth.limo/general/2021/01/26/snarks.html) or the [World Economic Forum report on blockchain privacy](https://www.weforum.org/reports/building-blockchain-privacy).
Applications for OEMs and Suppliers
ZK pseudonyms can transform supplier collaboration in several ways:- Carbon Reporting: Prove emissions compliance without exposing detailed process data.- Material Composition: Show regulatory compliance without disclosing proprietary recipes.- Labor Standards: Validate certifications without revealing HR records.- Financial Health: Demonstrate solvency without sharing full balance sheets.Each of these use cases enables OEMs to access verifiable trust while suppliers retain privacy.
Building Trust Through Privacy
Privacy-by-design approaches like ZK proofs flip the narrative: instead of demanding full disclosure, they enable selective disclosure. Suppliers gain confidence that sensitive details won’t be exposed, making them more willing to participate in digital ecosystems. OEMs get cryptographic guarantees they can trust, without the burden of managing sensitive supplier data themselves.
Closing Thoughts
ZK pseudonyms are not the silver bullet for supply chain privacy—but they are a powerful starting point. By embedding privacy into collaboration from the start, OEMs can break down barriers, strengthen trust, and unlock richer supplier data. As cryptographic technologies evolve, more advanced tools like MPC and homomorphic encryption will join the toolkit. But for today, Zero-Knowledge proofs offer a pragmatic, impactful way to balance transparency with confidentiality.
In the next discussion, we’ll explore how these privacy-preserving tools integrate into broader supply chain resilience strategies, linking operational visibility with governance and finance.





Comments